iptables: IP Packets's Flow
One picture is better than thousand words. If you don’t understand how iptables work in my previous post about secure Linux gateway, it is because you don’t know how it works and what the chains are. To understand iptables’s flow at a glance, I found a brief explanation at IP Masquerading (NAT) using iptables.
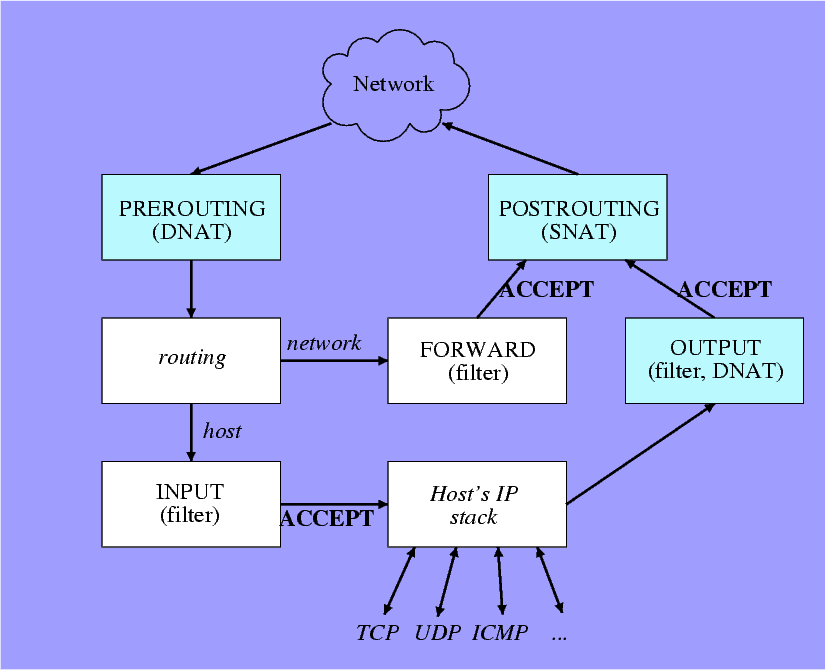
In conclusion, there are 2 classes of chains.
- nat
- PREROUTING
- OUTPUT
- POSTROUTING
- filter
- INPUT
- FORWARD
- OUTPUT
All incoming packets are passed through PREROUTING chain and next to routing process. If you want to block packets to both host itself and other networks, PREROUTING is the place you have to add filter. After the packets are routed, they are classified as local packets or network packets. Local packets mean their destination is the local host and network packets mean their destination is remote host. For local packets, they are passed to INPUT chain, next to host’s IP stack. The local IP stack may pump out packets to the network. All outgoing packets originated by local host are passed to OUTPUT chain. In particular, remote packets are passed to FORWARD chain.. All packets then are passed to POSTROUTING and next to the network. Below is my brief conclusion how to choose the right chain.
- PREROUTING - Filter all incoming packets no matter what they are sent to local host or not
- INPUT - Filter incoming packets sent to local host only
- FORWARD - Filter incoming packets sent to remote host only (being routed to remote host)
- OUTPUT - Filter outgoing packets sent to the networks
- POSTROUTING - Filter all outgoing packets
Technorati Tags: English, IT, Security, Software, Linux, Tips and Tricks, Iptables, Firewall, Router, Gateway
- sugree's blog
- 2142 reads


Post new comment