Security
iptables: IP Packets's Flow
One picture is better than thousand words. If you don’t understand how iptables work in my previous post about secure Linux gateway, it is because you don’t know how it works and what the chains are. To understand iptables’s flow at a glance, I found a brief explanation at IP Masquerading (NAT) using iptables.
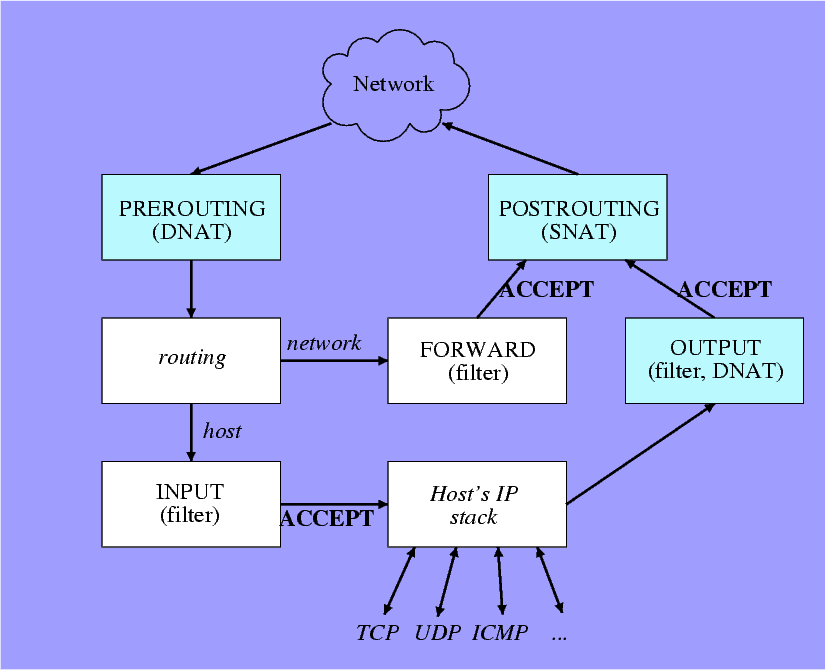
- sugree's blog
- Add new comment
- Read more
- 2421 reads

Setup secure Linux gateway using iptables
Nowadays, you might have a network of computers linked as an intranet and you want to let them read/reply e-mail. So you have to connect them to Internet by something. The key component is a router aka gateway. You might just buy an ADSL router with RJ45 port. Anyway, in case of you have too many machines, ADSL router maybe unable to handle all requests successfully due to design limitation. For example, ZyXEL Prestige 650-R can only handle 1024 concurrent connections. If the router has 1024 concurrent connections, next connection will be dropped silently.
- sugree's blog
- Add new comment
- Read more
- 1270 reads

Sessions in ZyXEL Prestige 650 Series
If you are using ZyXEL Prestige 650 Series, e.g. Prestige 650-R, like me, you must be aware of its limitation. According to its support note, this router does not limit the number of the users but the number of the sessions. In particular, the Prestige 650 supports concurrent 1024 sessions. A session is an end-to-end pair of two IP addresses. For example, whenever you view a web page, you are probably establishing 1 to 10 sessions depending on browser settings, internal frames, and images in that page. Instant messengers hold at least one connection. Assuming that a machine will always establish at least 10 connections, as a result, there are approximately 500 sessions for 50 machines. For more precisely, you can view the active sessions using telnet interface. Just follow below procedure.
- sugree's blog
- Add new comment
- Read more
- 842 reads

Dtrace และ SystemTap
พอดีลองวนๆ ไปหาอะไรอ่านเกี่ยวกับ project ที่ RH ดำเนินการอยู่พอดีไปเอะใจตรง SystemTab project ลองไปไล่ๆ อ่านดูทำไม concept เหมือน DTrace เลยหว่า
ลองอ่านๆ ในส่วนของ architecture ดูอืมม ไม่เหมือนแค่ concept ด้วยเห่ะ ทำงานยังคล้ายๆ กันเลย ใครสนใจลองไปดูได้ architecture paper (July 2005)
- zendz's blog
- Add new comment
- Read more
- 1966 reads

Google has been sued in many copyright cases because anyone can get information what they want from Google directly without purchasing them from the owner. One of a case is the sue by Perfect 10, a nude photo website, on 2004. Eventually, the court . So Google is going to get Perfect 10 out of its index and cache by the end of this month, or exactly by March 8.
- sugree's blog
- Add new comment
- 1027 reads

Living with phpBB
phpBB is a powerful and popular bulletin board software running on top of PHP and mySQL. However, you will get some trouble to use so popular softwares. Can you guess what kind of trouble you will get from phpBB? It is a very simple one. If you have deployed phpBB for a year you could encounter this situation. Yes, it is hacked again and again.
My friend is providing hosting services on FreeBSD server. This server is very secure. However, it was hacked 2 days ago through phpBB deployed by his customer himself. The result is that the hacker successfully added a cron entry to run IRC bot. Then he found that the installed phpBB had at least a vulnerability relating to mishandling string.
- sugree's blog
- 20 comments
- Read more
- 192095 reads


Recent comments
3 years 3 weeks ago
3 years 8 weeks ago
3 years 8 weeks ago
3 years 9 weeks ago
3 years 9 weeks ago
3 years 11 weeks ago
3 years 11 weeks ago
3 years 12 weeks ago
3 years 12 weeks ago
3 years 12 weeks ago